micro_res: Epistemology of electromagnetic waves with Shintaro Miyazaki
Table of Contents
Epistemology of electromagnetic waves [with Shintaro Miyazaki]
- May 25-29 2009
- Micro-residency research notes
Surrounded by invisible electromagnetic waves we live in an age of unhearable cacophonies. Serial coded signals and their rhythms are flying around us making a kind of unheard music.The investigations try to analyse those signals and reconstruct their content using contemporary technologies such as software-defined radio (USRP) and is a collaboration between mediatheorist and archeologist Shintaro Miyazaki and practitioner Martin Howse.
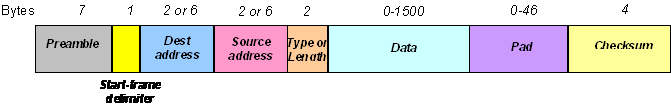
Investigating the physical/protocol bridge:
http://en.wikipedia.org/wiki/Physical\_layer
- Videos:
background notes
about ethernet/10/100BASE-T
http://en.wikipedia.org/wiki/Ethernet\_physical\_layer
manchester encoding (10BASE-T):
http://en.wikipedia.org/wiki/Manchester\_code
100BASE-T:
4B5B MLT-3 coded signaling, CAT5 copper cabling with two twisted pairs.
refs:
wireshark
libpcap format
gnuradio
- questions
- what is negative frequency?
- real and complex/I and Q=quadrature
for LFRX (NOT quadrature?)
for DBSRX-LF (quad)
RX_MUX
also:
1.33.3.8) is_quadrature () Type Sub Function Return True if this daughterboard does quadrature up or down conversion. That is, Description return True if this board requires both I & Q analog channels. For this board, return False Usage db_basic.db_ lf _rx.is_quadrature()
- what is negative frequency?
- to baudline
:./usrp_rx_cfile.py -f 1070000 -d 64 /dev/stdout | /usr/bin/baudline -reset -samplerate 4000000 -channels 2 -quadrature -stdin
see if needs added -s ? (for short)
or:
/root/gnuradio/gr-utils/src/python/usrp_rx_cfile.py -d 16 -R B -f 2.41G -d 128 pipe
and:
cat pipe | baudline -reset -format le32f -samplerate 4000000 -channels 2 -quadrature -stdin
- live
usrp_fft.py -d 128 -f 0 -R A:1
note also the use of GRC (Gnu Radio Companion)
- data collection and analysis/plotting:
1] gr-utils/src/python/usrp_rx_cfile.py
eg.
:usrp_rx_cfile.py –nsamples 500000 -f 0 -d 128 -R A:1 001.dat
plotting scripts:
http://www.swigerco.com/gnuradio/plotting.html
2] modified usrp_am_mw_rcv-file.py (for bandpass and file sink)
eg.
:python usrp_am_mw_rcv-file.py -f 12.004M -n tempestoutput.raw
(to audacity: import(ed) as 32bit float, 128000 Samples)
3] usrp_spectrum_sense.py and specsense.py
(in gijon_root)
:python specsense.py -d 32 -R B 2.4G 2.42G > testing_spec
(clean up with macro/search of C-q C-j SPC for newlines)
http://1010.co.uk/org/notes.html#sec-28.4
- links of interest
scapy
python scapy.py
p=sr1(IP(dst="www.slashdot.org")/ICMP()/"XXXXXXXXXXX") >>> str(p) 'E\x00\x00\'Kp@\x00\xf0\x01\xf0P\xd8"\xb50\xc0\xa8\x01\x19\x00\x00\xeeE\x00\x00\x00\x00XXXXXXXXXXX\x00\x00\x00\x00\x00\x00\x00' >>> hexdump(p) 0000 45 00 00 27 4B 70 40 00 F0 01 F0 50 D8 22 B5 30 E..'Kp@....P.".0 0010 C0 A8 01 19 00 00 EE 45 00 00 00 00 58 58 58 58 .......E....XXXX 0020 58 58 58 58 58 58 58 00 00 00 00 00 00 00 XXXXXXX.......
physical access/devices
- wireless/802.11
bbn/gnuradio code:
http://www.1010.co.uk/org/notes.html#sec-23
at:
/root/gijon_root/adroitgrdevel/gr-bbn/src/examples
wireless channels are 5Mhz apart (access point here is 2.41 GHz)
eg:
:./bbn_80211b_rx.py -R B -f 2.41G -v -b -S 4
with beacons/data recorded to: pkt_data.txt
how this could be interpreted also by scapy or wireshark - match the packets
see also:
https://www.cgran.org/browser/projects/bbn\_80211/branches/douggeiger
Daily log
MON 25
http://www.mail-archive.com/discuss-gnuradio@gnu.org/msg15604.html
http://www.mail-archive.com/discuss-gnuradio@gnu.org/msg09470.html
:/root/gnuradio/gr-utils/src/python/usrp_rx_cfile.py -R A -f 0 -s -8 -d 16 test_cfile1.raw
is 8 bit short which should be SIGNED according to:
http://www.mail-archive.com/discuss-gnuradio@gnu.org/msg11392.html
??? is interleaved even with LFRX - look at the values
:.octaverc -> addpath(":~/gnuradio/gnuradio-core/src/utils");
:d = read_complex_binary('test_cfile_floatofff.raw', 1e6);
:plot(real(d(1000:24000)))
interleaved with zero from second null channel? yes (if frequency is set to 0)
is signed short 16 bits even when we have as 8 bits over USB? yes
TUE 26:
minimum decimation is 4: ADC is 64 MS/s so we have 16 MS/s
switched back to 10baseT (10 MHz?) on one laptop (other autonegotiates):
:mii-tool eth2 -F 10baseT-HD
looking into 4 bit samples over USB from USRP to increase sample rate (otherwise we appear to filter higher frequencies of Manchester encode 10-Base-T):
http://www.mail-archive.com/discuss-gnuradio@gnu.org/msg12970.html
http://www.mail-archive.com/discuss-gnuradio@gnu.org/msg16821.html
http://inkscape-forum.andreas-s.net/topic/99625
we can easily see 1010 preamble in audacity (16 bit signed/little endian/stereo):
[one x and many x's embedded in ICMP ping packet]
[and in close up]
but we do not see any 0s which can be embedded in packet using scapy:
:p=sr1(IP(dst="192.168.1.1")/ICMP()/"\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00")
[\x to embed hex]
packet and characters are easily identifiable with each sample point at approx 60 ns but we are not sampling fast enough - note that 10101010 (AA in hex) gives us the longest Manchester encoded transition.
scapy links:
http://www.secdev.org/projects/scapy/doc/
http://www.secdev.org/projects/scapy/doc/usage.html#interactive-tutorial
other gnuradio links:
http://www.snowymtn.ca/gnuradio/gnuradiodoc-4.pdf
https://radioware.nd.edu/documentation/hardware/the-usrp-board
WED 27
TODO:
- change impedance of input to USRP
no results/lowered gain
- change centre frequency just to see if this has any effect/also look at gain
centre frequency changes appearance of wave forms (also now we have 2 channels I and Q) but still not readable data
gain doesn't help
- look at scapy more with Ethernet frames
http://www.cse.iitm.ac.in/~jvimal/cs410/arp-spoof.txt
send Ethernet frame/packet:
:p=Ether()/IP(dst="192.168.1.1")/ICMP()/"xxxxx"
:sendp(p)
further:
:ls() - lists supported layers
:ls(Raw) - shows layer options
so: p=Ether()/IP(dst="192.168.1.1")/Raw(load="x")
or:
p=Ether()/IP(dst="192.168.1.1")/Raw(load="xo"*500) p.show2() str(p) ls(Dot11Beacon)
but we need frame injection capabilities, see also:
http://802.11ninja.net/lorcon/wiki/WiresharkWiFiInjection
and:
next up - mess with data from./bbn_80211b_rx.py -R B -d 8 -f 2412e6 -b
// note 802.11 channels are 5 MHz apart. channel 1 is at 2.412G (2412 MHz)
http://oss.netboxblue.com/pug/scapy.html
http://trac.secdev.org/scapy/wiki/BuildAndDissect
we can get straight hexdump data into scapy:
:a=import_hexcap()
then paste in hexdump all > Ctrl-D
then:
:a.show()
- also look into sox for raw data -> wav and gnuplot possibilities (conversion of data first)
:sox -r 441000 -s -c 2 -2 baseT2_transfer_bluewires_decim4_lessx.raw -c 1 -r 44100 testsox.wav
to convert to single channel wav
C code for 2 channel signed short -> decimal list for gnuplot:
modified raw2num and:
./raw2num ~/projects/shintaro_res/test_cfile1.raw testraw2num 1 100000
investigation of bluetooth:
Bluetooth uses a radio technology called frequency-hopping spread spectrum, which chops up the data being sent and transmits chunks of it on up to 79 frequencies. In its basic mode, the modulation is Gaussian frequency-shift keying (GFSK). It can achieve a gross data rate of 1 Mb/s.
2.408G
Bluesniff: http://www.usenix.org/event/woot07/tech/full\_papers/spill/spill\_html/
with reference there to GNUradio work packaged at:
http://www.cs.ucl.ac.uk/staff/a.bittau/gr-bluetooth.tar.gz
(to be ported from blks)
THU 28
what layer/protocol are packets captured by:
bbn_80211b_rx.py
802.11 physical layer ? (but what is physical layer - spread spectrum?)
:p=sr1(IP(dst="192.168.1.1")/ICMP()/("\xff\x00"*400)*1000)
creates large multiple ping packets
links:
http://www.wireless-bern.ch/?p=1444
http://osdir.com/ml/security.scapy.general/2007-11/msg00017.html
FRI 29
port bbn_80211b_tap.py and test with wireshark on tap interface
(ported with a few changes
~/projects/shintaro_res/projects/bbn_80211/branches/douggeiger/src/examples
creates gr0 which we then ifconfig and then sniff with wireshark
but doesn't seem to give satisfactory results)
- capture of beacon frames in wireshark:
ifconfig wlan0 down iw dev wlan0 interface add mon0 type monitor ifconfig mon0 up
and then using mon0 to capture in wireshark shows:
1] captured packets are around 91-300 bytes // those we get with bbn are maximum 40 bytes
2] layers: Radiotap header/beacon frame/wireless Lan management frame
try this with scapy??? but why so short????
for bbn source address is after 22 bytes (although in code is:
data_hdr = struct.unpack("@BBBBBB", packet_data[10:16]) mac_str = "%02x:%02x:%02x:%02x:%02X:%02X" % \ (data_hdr[0], data_hdr[1], data_hdr[2], data_hdr[3], data_hdr[4], data_hdr[5],)in wireshark is in IEEE 802.11 Beacon frame 35 bytes in//
[also we only seem to get Beacon frames in wireshark whereas some packets from da;9c laptop appear in bbn sniff]
also try:
tcpdump -s 0 -i mon0
[packet injection and iwl3945 wireless chipset in x60????]
SAT 30 [post-residency]
still trying to parse the bbn captured packet
most likely as radiotap header and Dot11ProbeReq
finally we arrive at:
>>> a=RadioTap(import_hexcap())
00000000 80 9a e9 00 00 00 00 00 24 00 df 14 40 00 00 00
00000010 00 ff ff ff ff ff 00 02 2d 0a da 9c ff ff ff ff
00000020 ff ff 00 16 00 04 31 30 31 30 01 04 02 04 0b 16
>>> a.show()
###[ RadioTap dummy ]###
version= 128
pad= 154
len= 233
present=
notdecoded= '$\x00\xdf\x14@\x00\x00\x00\x00\xff\xff\xff\xff\xff\x00\x02-\n\xda\x9c\xff\xff\xff\xff\xff\xff\x00\x16\x00\x041010\x01\x04\x02\x04\x0b\x16'
# we pad with three zeroes (why I know not to arrive at):
>>> p=Dot11('\00\x00\x00\x00\xdf\x14@\x00\x00\x00\x00\xff\xff\xff\xff\xff\x00\x02-\n\xda\x9c\xff\xff\xff\xff\xff\xff\x00\x16\x00\x041010\x01\x04\x02\x04\x0b\x16')
>>> p.show()
###[ 802.11 ]###
subtype= 0L
type= Management
proto= 0L
FCfield=
ID= 0
addr1= df:14:40:00:00:00
addr2= 00:ff:ff:ff:ff:ff
addr3= 00:02:2d:0a:da:9c
SC= 65535
addr4= None
###[ 802.11 Association Request ]###
cap= res8+res9+short-slot+res11+res12+DSSS-OFDM+res14+res15+ESS+IBSS+CFP+CFP-req+privacy+short-preamble+PBCC+agility
listen_interval= 65535
###[ 802.11 Information Element ]###
ID= SSID
len= 22
info= '\x00\x041010\x01\x04\x02\x04\x0b\x16'
>>>
addr3 is address of source of association request (does this match up?)
some links:
http://web.cecs.pdx.edu/~jrb/netsec/lectures/80211/associate.txt
http://evanjones.ca/software/fakeaps.c
http://trac.secdev.org/scapy/ticket/30
http://trac.secdev.org/scapy/ticket/109
http://osdir.com/ml/security.scapy.general/2008-04/msg00007.html
examples as audio files
Ethernet 10Base-T
Large single ping packet:
http://www.archive.org/details/thunetbigpingd4.wav
scp data transfer:
http://www.archive.org/details/thunettransferd4.wav
Recorded using USRP+LFRX, Gnuradio and command:
:./usrp_rx_cfile.py -s -8 -R A -f 0M -d 4 thunetAAd4.raw
[8 bit samples over the USB bus, tuned to 0MHz, decimation of 4]
[into audacity: Import raw data, Signed 16 bit PCM, Little Endian, Stereo, 100000 Hz sample rate - slowed down also in effects by 99%]
Bluetooth
Bluetooth data transfer:
http://www.archive.org/details/wed\_bluetooth2.4.08.wav
:/usrp_rx_cfile.py -s -8 -R B -f 2408M -d 4 wed_bluetooth2.4.08.raw
- audacity with no slow down.
802.11
802.11 WEP password packet:
http://www.archive.org/details/thu2462Mwep\_pass4.wav
/usrp_rx_cfile.py -g 48 -s -8 -R B -f 2462M -d 4 thu2462Mwep_pass4.raw
- audacity slowed down
Date: 2010-11-26 16:49:43 GMT
HTML generated by org-mode 6.31trans in emacs 23